What's On
The Lord Mayor of the , Alastair King, has today…
Going Out
Little Simz has announced a pair of gigs which will…
Reviews
Martin Mayer’s shiny, new production, it turns out, is almost…
Latest Articles
The best gifts you can buy for gamers” datanexthead/>nAs a consumer journalist, Pete has reviewed hundreds of products…
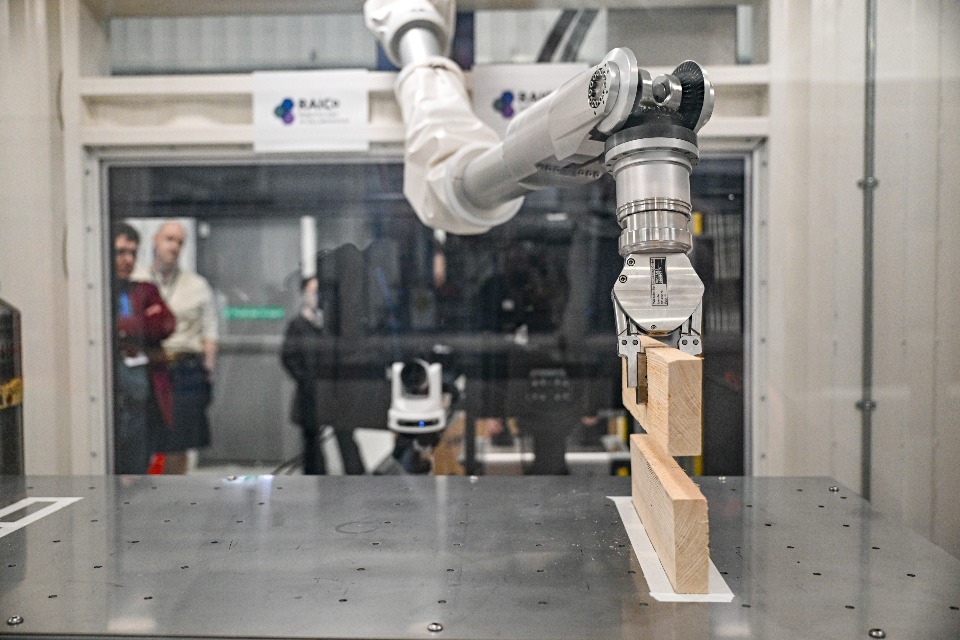
The week-long workshop showcased best practice in innovative technologies to support nuclear decommissioning. Held at Energus in West…
Louise Smyth CBE, Chief Executive of Companies House and Registrar of Companies for England and Wales will be…
Crayfish plague, which is normally spread by invasive American signal crayfish, is deadly for the native species and…
The British High Commission is proud to announce winners for the fourth annual Ambassador for a Day (AfD)…
Good afternoon everyone, I’m sorry I can’t join you in person, but I am delighted to join my…
In response to increased findings of highly pathogenic avian influenza (’bird flu’) in wild birds and new cases…
Mr President, I have the honour to present draft resolution L.25 on the human rights situation in the…
In Spotlight
For almost 100 years, Disney has produced countless animated classics…